Candidates use the latest updated Cisco Certified DevNet Professional (CCDP) 300-920 dumps from leads4pass: https://www.leads4pass.com/300-920.html, to help you get past the hurdle and successfully pass the 300-920 DEVWBX exam.
leads4pass 300-920 dumps provide PDF files and a VCE exam engine to help you practice 300-920 DEVWBX exam questions quickly and easily. The latest updated 300-920 dumps contain 60 exam questions and answers, verified by IT experts to be true and effective.
Share 13 CCDP 300-920 dumps PDF:https://drive.google.com/file/d/1qSUFaHY2T85dweGiJgUn5RVDy8RRukVE/
Read CCDP 300-920 dumps exam questions and answers online:
| Number of exam questions | Exam name | Release time | From | Previous issue |
| 15 | Developing Applications for Cisco Webex and Webex Devices (DEVWBX) | Sep 21, 2022 | leads4pass | Aug 26, 2022 |
New Question 1:
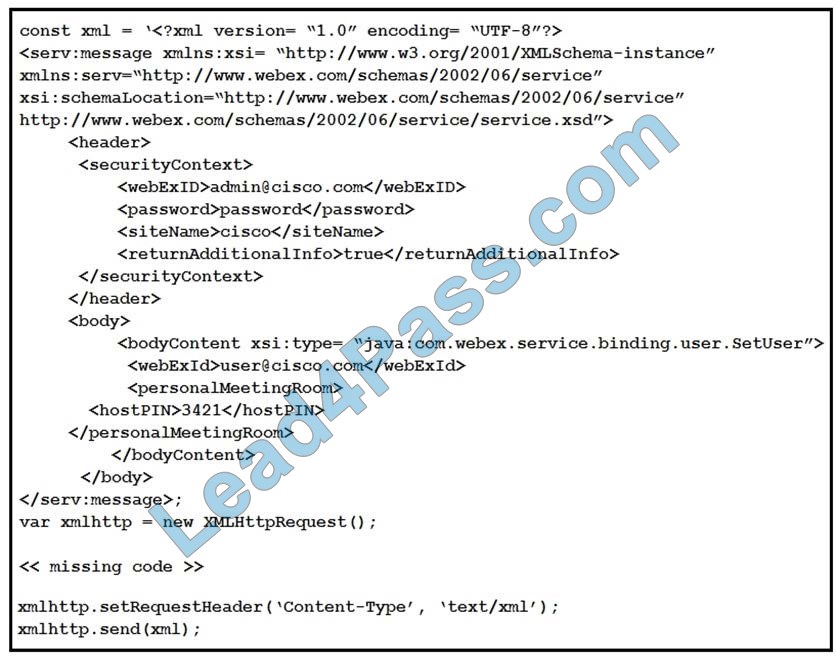
Refer to the exhibit. A developer must construct an HTTP Request to use the XML API to set a Personal Meeting Room PIN for a given user. Which code completes the code to create the request?
A. xmlhttp.open("GET", "https://cisco.webex.com/WBXService/XMLService");
B. xmlhttp.open("PATCH", "https://cisco.webex.com/WBXService/XMLService");
C. xmlhttp.open("PUT", "https://cisco.webex.com/WBXService/XMLService");
D. xmlhttp.open("POST", "https://cisco.webex.com/WBXService/XMLService");
Correct Answer: D
The post method can be used for the HTTP request that sets up a personal meeting room PIN for a user.
New Question 2:
Which expression is a valid Webex Teams webhook filter?
A. [email protected]+roomId=abc123
B. [email protected]=abc123
C. [email protected]=abc123
D. [email protected],roomId=abc123
Correct Answer: C
You can also use more than one filter in a webhook. To use multiple filters, combine them with the "and" symbol. For example, to create a webhook that only sends notifications when a specific person performs an action in a specific room, such as sending a message or creating a membership, combine the personEmail and roomId filters.
Reference: https://developer.webex.com/docs/api/guides/webhooks
New Question 3:
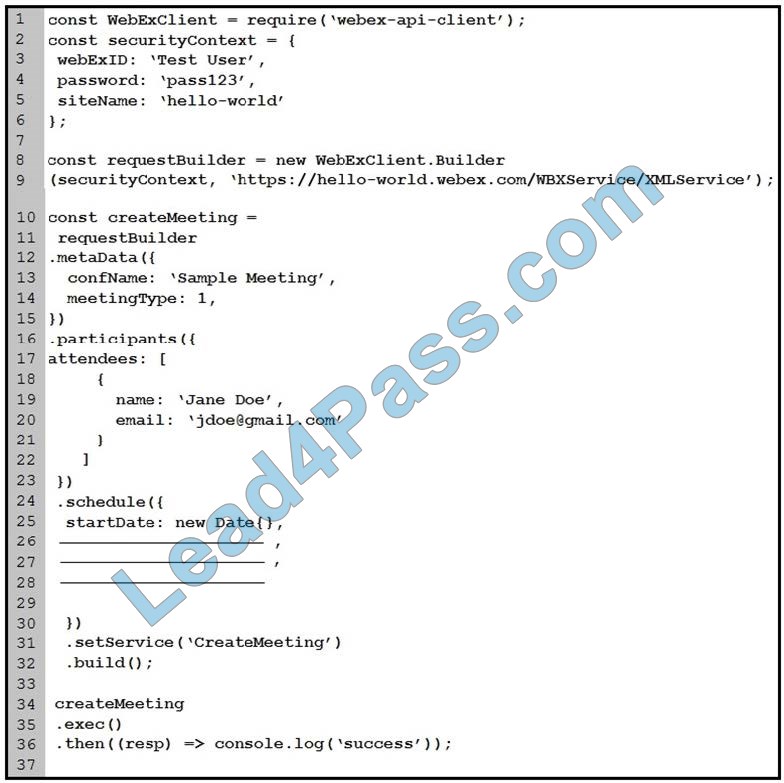
Refer to the exhibit. Which code for blank lines 26, 27, and 28 gives invitees 900 seconds before the scheduled time to join the meeting, sets the meeting to last for 30 minutes, and sets the meeting timezone to Pacific US?
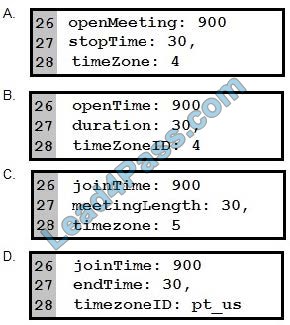
A. Option A
B. Option B
C. Option C
D. Option D
Correct Answer: B
Reference: https://github.com/cisco-ie/webex-api-client
New Question 4:
Which two items are needed to give a Webex user the ability to archive all Webex Teams messages for an organization? (Choose two.)
A. Give the user "Read-only administrator privileges" in the Webex Control Hub.
B. Create an Integration app with all "spark_compliance" read scopes enabled.
C. Use the Webex Meetings XML API "SetUser" to update the user\'s "" value to "TRUE".
D. Configure the user as a "Compliance Officer" in the Webex Control Hub.
E. Create a Bot app with all "webex_compliance" read scopes enabled.
Correct Answer: AD
New Question 5:
What happens if a meeting is in progress when a DelMeeting request is sent in the Webex Meetings XML API?
A. The meeting host is notified and prompted to allow the meeting to be deleted.
B. The DelMeeting request drops all call-in users and deletes the meeting.
C. The DelMeeting request waits until the meeting is completed and then deletes the meeting.
D. The DelMeeting request results in an error.
Correct Answer: A
Reference: https://pdfslide.net/documents/webex-we.html (p.216)
New Question 6:
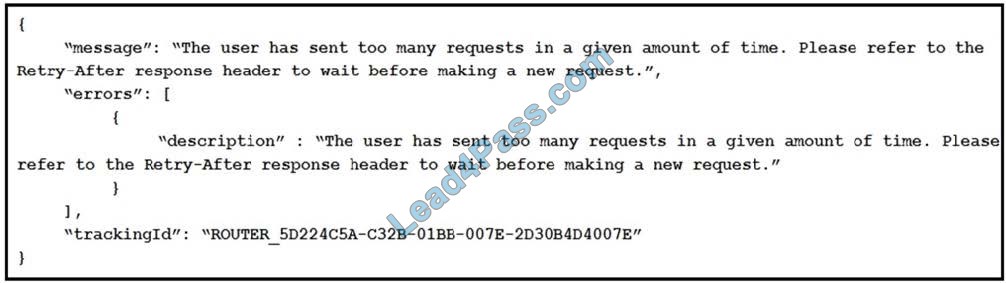
Refer to the exhibit. What is the Webex Teams REST API HTTP response status code, based on this code snippet?
A. 401
B. 403
C. 429
D. 501
Correct Answer: C
Reference: https://developer.webex.com/docs/api/v1/messages/get-message-details
New Question 7:
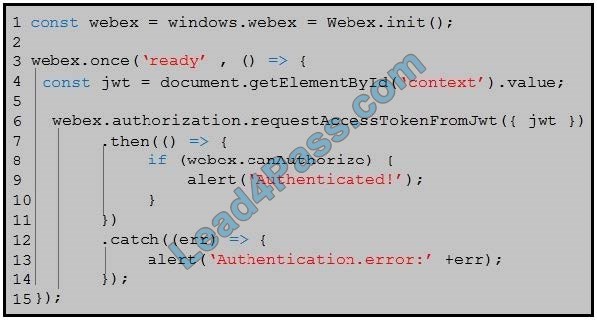
Refer to the exhibit. On line 4, the script retrieves a context from a DOM element that was generated from a server-side component. How does that server-side component obtain the value for the `context\' element?
A. by opening a dialog asking the end-user to paste his personal access token
B. by completing an authorization code grant flow using the identifier and secret of an OAuth integration
C. by embedding the access token of a Bot account
D. by creating a guest token using the identifier and secret of a Guest Issuer application
Correct Answer: B
New Question 8:
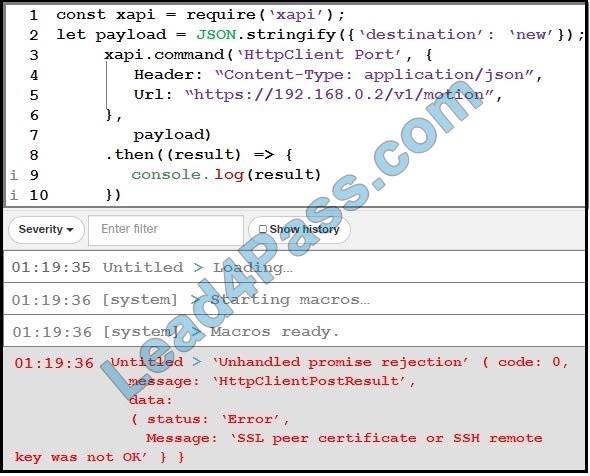
Refer to the exhibit. What causes the error message?
A. xapi must be enabled for promises.
B. HttpClient AllowInsecureHTTPS has not been enabled.
C. The NODE_TLS_REJECT_UNAUTHORIZED environment variable must be set to 0.
D. HttpClient must be changes to HttpsClient.
Correct Answer: B
Reference: https://help.webex.com/en-us/nthg6le/Sending-HTTP-Requests-from-a-Board-Room-or-Desk-Device
New Question 9:
A Webex Teams bot is deployed but soon it stops responding. Which two explanations are the cause of the issue? (Choose two.)
A. A new webhook was created, which marks the old webhook as inactive.
B. The web server that is set to receive webhooks is not configured to return a 200 message. And the webhook is disabled.
C. The webhook secret is expired and must be refreshed.
D. The refresh token is not being used.
E. The bot owner regenerated the access token on developer.webex.com.
Correct Answer: AB
Reference: https://developer.authorize.net/api/reference/features/webhooks.html
New Question 10:
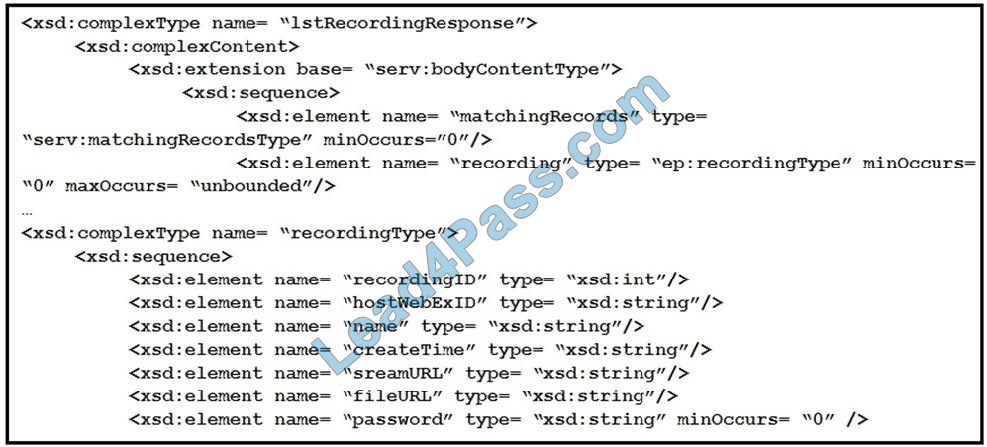
Refer to the exhibit. A snippet from the XSD schema of the Webex Meeting XML API LstRecordingResponse\' element is listed in the exhibit. Assuming that a variable namedresp\' exists that contains the XML response from a successful `LstRecording\' request, which code snippet correctly generates a simple report that lists meeting names and recording file download links?
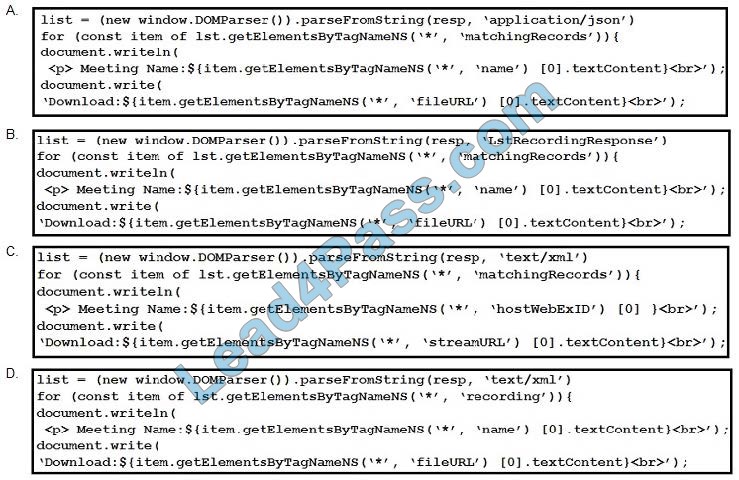
A. Option A
B. Option B
C. Option C
D. Option D
Correct Answer: A
New Question 11:
With CE 9.8 and above, which two statements are correct when an application is sending and receiving data over a connection established with an xAPI interface? (Choose two.)
A. All Serial, SSH, and WebSockets can be used to send and receive data.
B. HttpClient can be used to send requests but not receive responses.
C. HttpFeedback is the only option to receive data.
D. The HttpClient command can be used to send requests and read responses over HTTP.
E. WebSockets is the only option to send and receive data.
Correct Answer: BD
New Question 12:
Which element is needed to build a Web application that authenticates Webex users and can post messages under the user\'s identity?
A. OAuth integration configured with the `messages_write\' scope
B. bot access token
C. Guest Issuer application
D. self-signed certificate that is created by a public authority
Correct Answer: A
Reference: https://developer.webex.com/blog/real-world-walkthrough-of-building-an-oauth-webex-integration
New Question 13:
Which two filters are valid for limiting a webhook? (Choose two.)
A. roomId=
B. personId!=
C. spaceId=
D. personId=$spaceId=
E. personId=$roomId=
Correct Answer: AB
Reference: https://developer.webex.com/docs/api/guides/webhooks
New Question 14:
Which Webex Teams webhook resource type indicates that a user interacted with a card?
A. buttonActions
B. attachmentActions
C. webhookCardActions
D. cardActions
Correct Answer: B
Reference: https://developer.webex.com/docs/api/guides/webhooks
New Question 15:
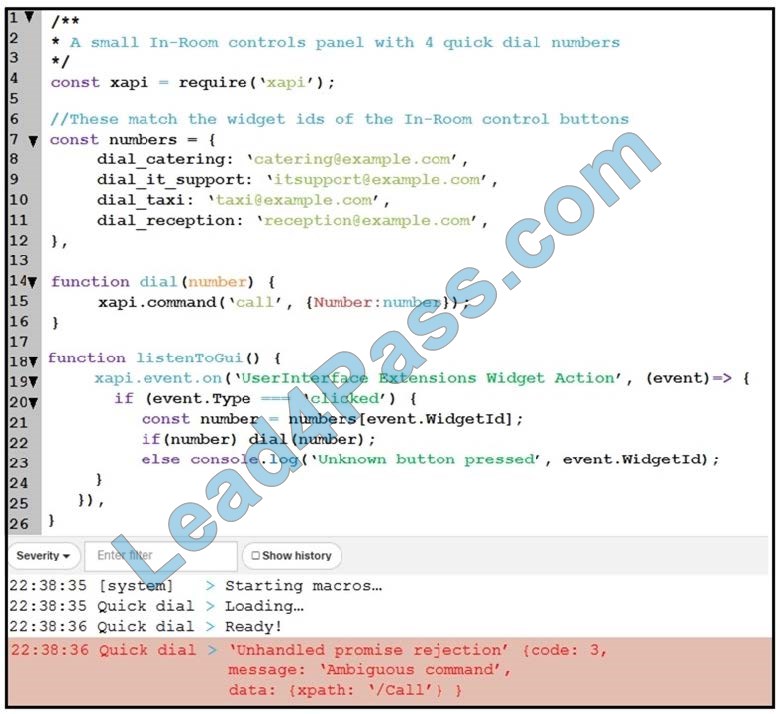
Refer to the exhibit. An end user reports that the speed dial button is not working on their Webex Device, and when loading into the Macro Editor, this error was presented. On which line is the incorrect syntax?
A. line 4
B. line 14
C. line 15
D. line 22
Correct Answer: C
...
Download 13 CCDP 300-920 dumps PDF:https://drive.google.com/file/d/1qSUFaHY2T85dweGiJgUn5RVDy8RRukVE/
Candidates studying the CCDP 300-920 dumps exam questions above can help them improve their exam experience, but this is only a warm-up.
You are welcome to download the latest updated CCDP 300-920 dumps: https://www.leads4pass.com/300-920.html, A truly effective route for candidates to pass the 300-920 DEVWBX exam.