? We only share the latest and effective actual test questions and answers!
leads4pass shares the latest and effective SC-200 dumps to help pass the SC-200 exam: "Microsoft Identity and Access Administrator"! leads4pass SC-200 Dumps includes SC-200 VCE dumps and SC-200 PDF dumps.
leads4pass SC-200 test questions have been updated to the latest date to ensure immediate validity. Get the latest leads4pass SC-200 dumps (PDF + VCE): https://www.leads4pass.com/sc-200.html (72 Q&A dumps)
Article content list:
- Get part of sc-200 pdf from google drive for free
- Part of Microsoft SC-200 exam practice questions from Youtube
- Real questions cracking Microsoft SC-200 exam questions practice test
- Get Microsoft exam discount code 2021
Get part of sc-200 pdf from google drive for free
Free share Microsoft SC-200 exam PDF from Google Drive provided by leads4pass
https://drive.google.com/file/d/1jgIN4dHX3CYWzGxYjtEsCF_pkdoM6J8P/
Microsoft SC-200 exam questions online practice test
QUESTION 1
You provision Azure Sentinel for a new Azure subscription.
You are configuring the Security Events connector.
While creating a new rule from a template in the connector, you decide to generate a new alert for every event.
You create the following rule query. 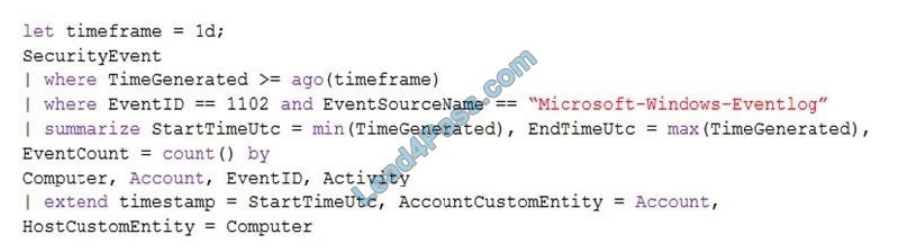
By which two components can you group alerts into incidents? Each correct answer presents a complete solution.
NOTE: Each correct selection is worth one point.
A. user
B. resource group
C. IP address
D. computer
Correct Answer: CD
QUESTION 2
You need to create the test rule to meet the Azure Sentinel requirements. What should you do when you create the
rule?
A. From Set rule logic, turn off suppression.
B. From Analytics rule details, configure the tactics.
C. From Set rule logic, map the entities.
D. From Analytics rule details, configure the severity.
Correct Answer: C
Reference: https://docs.microsoft.com/en-us/azure/sentinel/tutorial-detect-threats-custom
QUESTION 3
You plan to create a custom Azure Sentinel query that will provide a visual representation of the security alerts
generated by Azure Security Center.
You need to create a query that will be used to display a bar graph.
What should you include in the query?
A. extend
B. bin
C. count
D. workspace
Correct Answer: C
Reference: https://docs.microsoft.com/en-us/azure/azure-monitor/visualize/workbooks-chart-visualizations
QUESTION 4
You plan to create a custom Azure Sentinel query that will track anomalous Azure Active Directory (Azure AD) sign-in
activity and present the activity as a time chart aggregated by day.
You need to create a query that will be used to display the time chart.
What should you include in the query?
A. extend
B. bin
C. makeset
D. workspace
Correct Answer: B
Reference: https://docs.microsoft.com/en-us/azure/azure-monitor/logs/get-started-queries
QUESTION 5
The issue for which team can be resolved by using Microsoft Defender for Endpoint?
A. executive
B. sales
C. marketing
Correct Answer: B
Reference: https://docs.microsoft.com/en-us/windows/security/threat-protection/microsoft-defender-atp/microsoftdefender-atp-ios
QUESTION 6
DRAG-DROP
You have resources in Azure and Google cloud.
You need to ingest Google Cloud Platform (GCP) data into Azure Defender.
In which order should you perform the actions? To answer, move all actions from the list of actions to the answer area
and arrange them in the correct order.
Select and Place: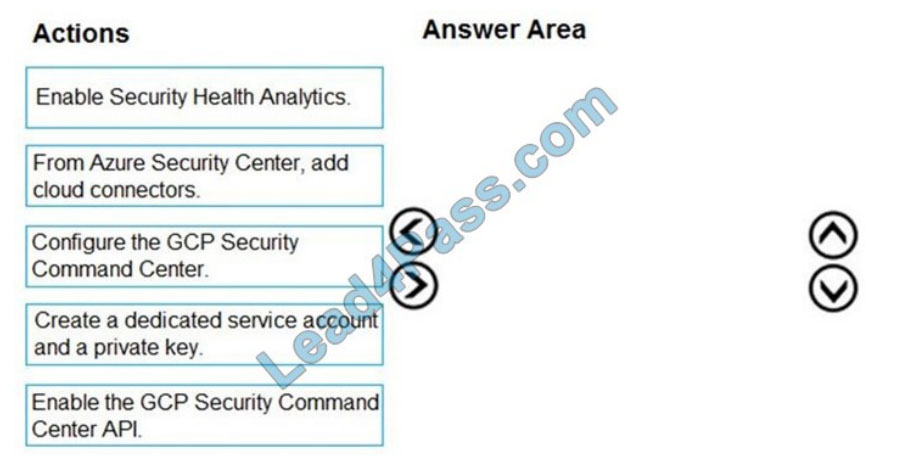
Correct Answer:
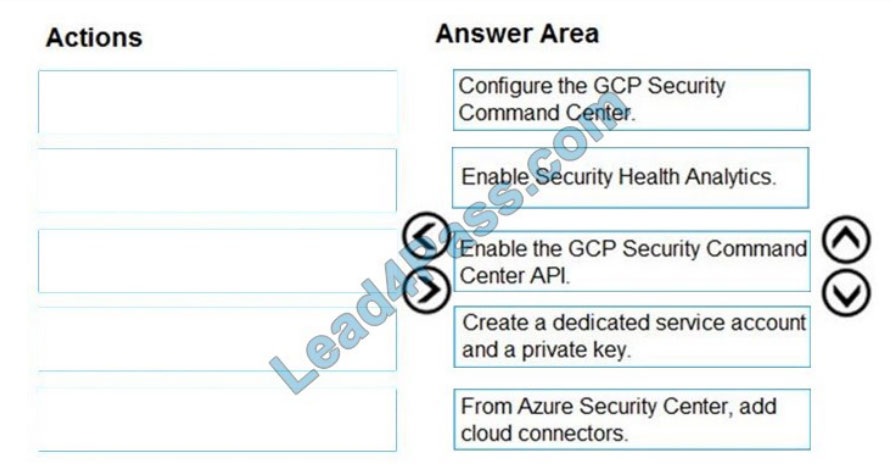
QUESTION 7
DRAG-DROP
You create a new Azure subscription and start collecting logs for Azure Monitor.
You need to configure Azure Security Center to detect possible threats related to sign-ins from suspicious IP addresses
to Azure virtual machines. The solution must validate the configuration.
Which three actions should you perform in a sequence? To answer, move the appropriate actions from the list of action
to the answer area and arrange them in the correct order.
Select and Place:
Correct Answer:
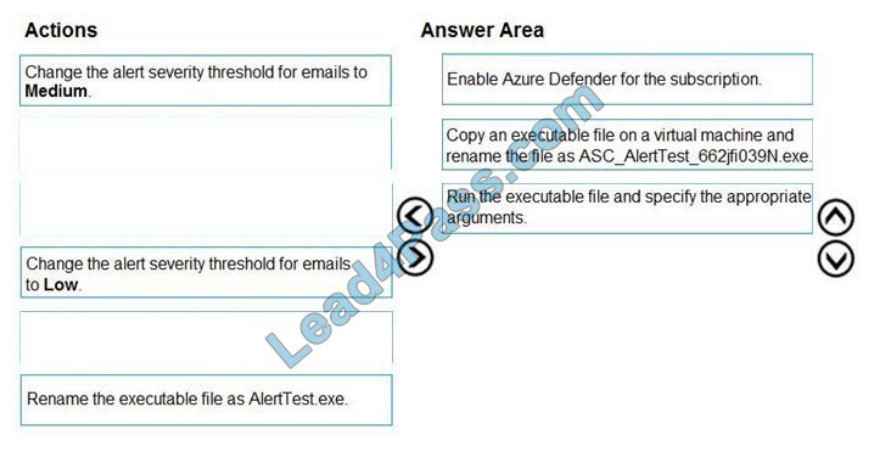
QUESTION 8
You need to visualize Azure Sentinel data and enrich the data by using third-party data sources to identify indicators of
compromise (IoC). What should you use?
A. notebooks in Azure Sentinel
B. Microsoft Cloud App Security
C. Azure Monitor
D. hunting queries in Azure Sentinel
Correct Answer: A
Reference: https://docs.microsoft.com/en-us/azure/sentinel/notebooks
QUESTION 9
DRAG-DROP
You open the Cloud App Security portal as shown in the following exhibit.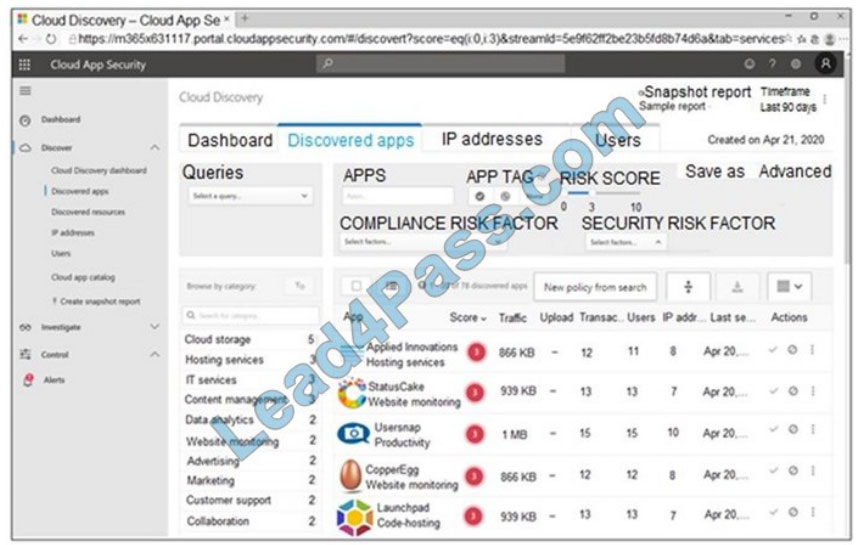
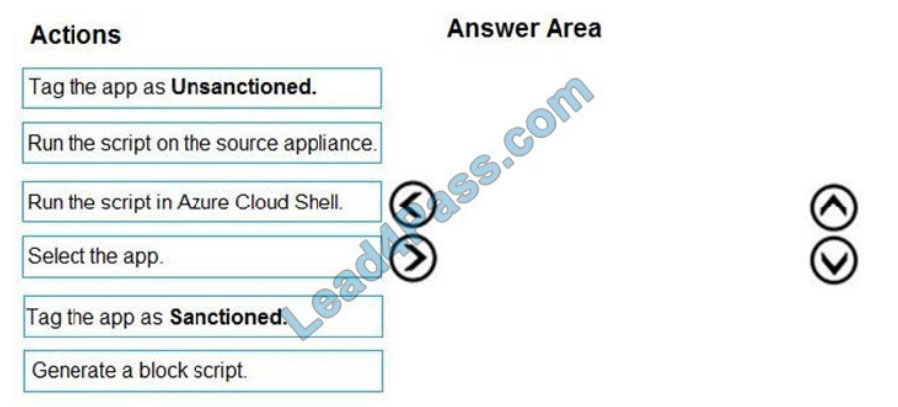
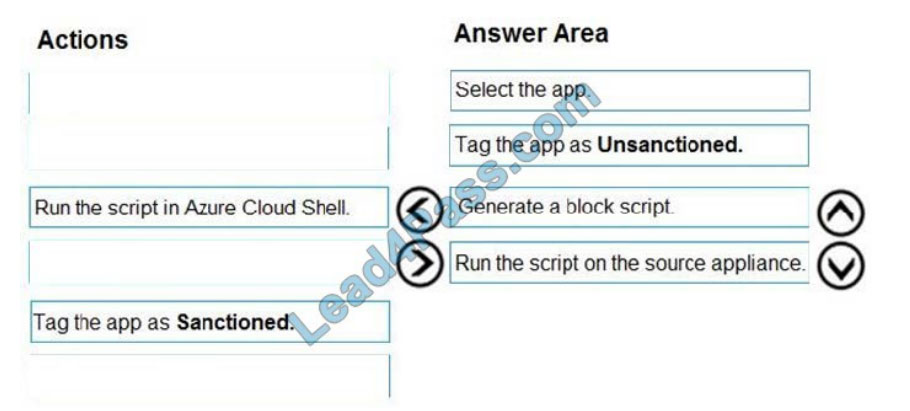
You need to remediate the risk for the Launchpad app.
Which four actions should you perform in sequence? To answer, move the appropriate actions from the list of actions to
the answer area and arrange them in the correct order.
Select and Place:
Correct Answer:
QUESTION 10
DRAG-DROP
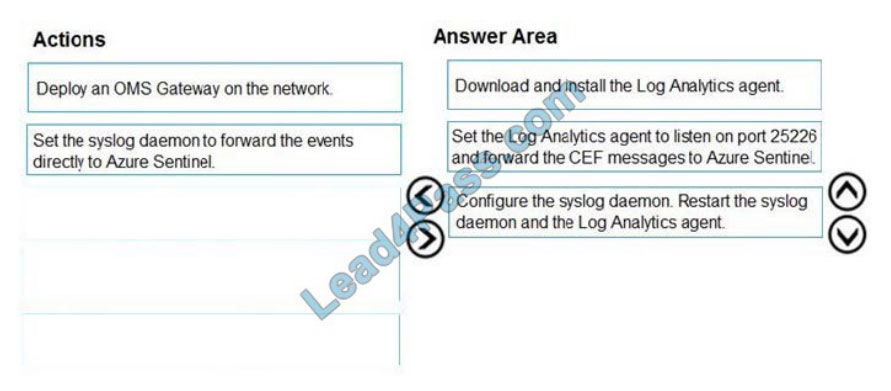
You plan to connect an external solution that will send Common Event Format (CEF) messages to Azure Sentinel.
You need to deploy the log forwarder.
Which three actions should you perform in sequence? To answer, move the appropriate actions from the list of actions
to the answer area and arrange them in the correct order.
Select and Place: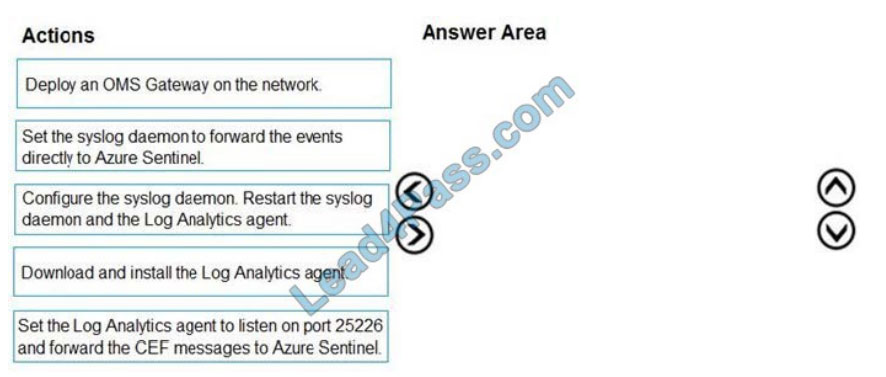
Correct Answer:
QUESTION 11
You have an existing Azure logic app that is used to block Azure Active Directory (Azure AD) users. The logic app is
triggered manually.
You deploy Azure Sentinel.
You need to use the existing logic app as a playbook in Azure Sentinel.
What should you do first?
A. And a new scheduled query rule.
B. Add a data connector to Azure Sentinel.
C. Configure a custom Threat Intelligence connector in Azure Sentinel.
D. Modify the trigger in the logic app.
Correct Answer: B
QUESTION 12
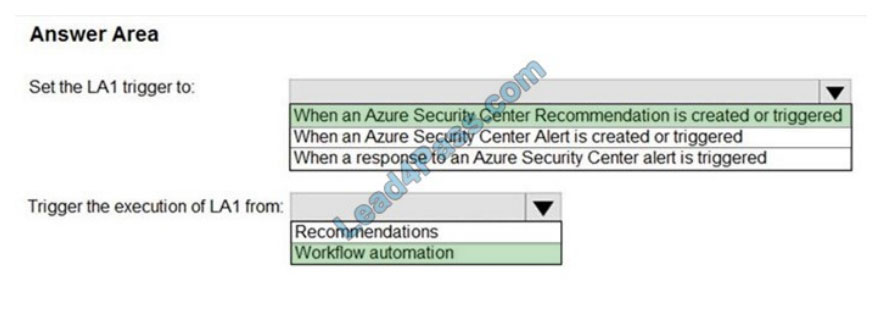
HOTSPOT
You have an Azure subscription that has Azure Defender enabled for all supported resource types.
You create an Azure logic app named LA1.
You plan to use LA1 to automatically remediate security risks detected in Azure Security Center.
You need to test LA1 in Security Center.
What should you do? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
Hot Area: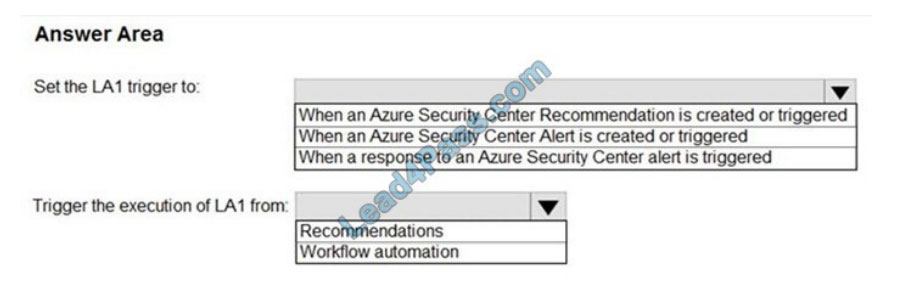
Correct Answer:
QUESTION 13
You have the following advanced hunting query in Microsoft 365 Defender.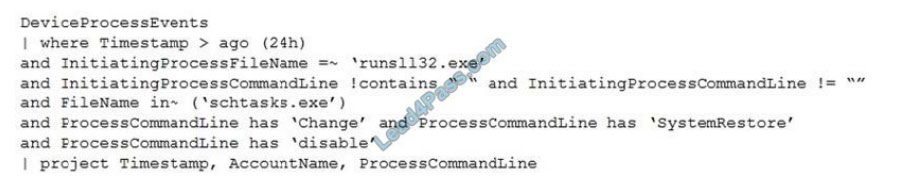
You need to receive an alert when any process disables System Restore on a device managed by Microsoft Defender
during the last 24 hours.
Which two actions should you perform? Each correct answer presents part of the solution.
NOTE: Each correct selection is worth one point.
A. Create a detection rule.
B. Create a suppression rule.
C. Add | order by Timestamp to the query.
D. Replace DeviceProcessEvents with DeviceNetworkEvents.
E. Add DeviceId and ReportId to the output of the query.
Correct Answer: AE
Reference: https://docs.microsoft.com/en-us/windows/security/threat-protection/microsoft-defender-atp/customdetection-rules
Get Microsoft exam discount code 2021
leads4pass In order to give back to our friends who have supported us for many years, we will share the latest exam discount codes every year
Thank you for reading! I have told you how to successfully pass the Microsoft SC-200 exam.
You can choose: https://www.leads4pass.com/sc-200.html to directly enter the SC-200 Exam dumps channel! Get the key to successfully pass the exam!
Wish you happiness!
Get free Microsoft SC-200 exam PDF online: https://drive.google.com/file/d/1jgIN4dHX3CYWzGxYjtEsCF_pkdoM6J8P/