What is the best way to pass the Microsoft 98-367 exam? (First: Exam practice test, Second: leads4pass Microsoft expert.) You can get free Microsoft IT Infrastructure 98-367 exam practice test questions here.
Or choose https://www.leads4pass.com/98-367.html (277 Q&As). Study hard to pass the exam easily!
Table of Contents:
- Latest Microsoft IT Infrastructure 98-367 google drive
- Effective Microsoft 98-367 exam practice questions
- Related 98-367 Popular Exam resources
- leads4pass Year-round Discount Code
- What are the advantages of leads4pass?
Latest Microsoft IT Infrastructure 98-367 google drive
[PDF] Free Microsoft IT Infrastructure 98-367 pdf dumps download from Google Drive: https://drive.google.com/open?id=14gwb7N7QVBYbfV2F1l-bH3gDl3On2hpT
Exam 98-367: Security fundamentals - Microsoft:https://www.microsoft.com/en-us/learning/exam-98-367.aspx
Skills measured
This exam measures your ability to accomplish the technical tasks listed below.
- Understand security layers (25–30%)
- Understand operating system security (35-40%)
- Understand network security (20–25%)
- Understand security software (15–20%)
Who should take this exam?
This exam validates that a candidate has fundamental security knowledge and skills. It can serve as a stepping stone to the Microsoft Certified Solutions Associate (MCSA) exams.
It is recommended that candidates become familiar with the concepts and the technologies described here by taking relevant training courses. Candidates are expected to have some hands-on experience with Windows Server, Windows-based networking, Active Directory, anti-malware products, firewalls, network topologies and devices, and network ports.
Latest updates Microsoft 98-367 exam practice questions
QUESTION 1
Which of the following is a tool that can be used to evaluate the servers having vulnerabilities that are related to the
operating system and installed software?
A. DNS dynamic update
B. Windows Software Update Services
C. Read-Only domain controller (RODC)
D. Microsoft Baseline Security Analyzer
Correct Answer: D
Microsoft Baseline Security Analyzer is a tool that can be used to evaluate the servers having vulnerabilities that are
related to the operating system and installed software Microsoft Baseline Security Analyzer (MBSA) is a software tool of
Microsoft to determine security state by assessing missing security updates and less- secure security settings within
Microsoft Windows, Windows components such as Internet Explorer, IIS web server, and products Microsoft SQL
Server,
and Microsoft Office macro settings. Microsoft Baseline Security Analyzer (MBSA) includes a graphical and command
line interface that can perform local or remote scans of Windows systems.
Answer: B is incorrect. Windows Server Update Services (WSUS) is an add- on component of Windows Server 2008. It
provides functionality to a server to run as a Windows Update server in a Windows network environment.
Administrators
can configure a WSUS server as the only server to download updates from Windows site, and configure other
computers on the network to use the server as the source of update files. This will save lots of bandwidth as each
computer will not
download updates individually. WSUS 3.0 SP1 is the only version of WSUS that can be installed on Windows Server
2008. Earlier versions of WSUS cannot be installed on a server running Windows Server 2008.
Answer: C is incorrect. Read-only Domain Controller (RODC) is a domain controller that hosts the read-only partition of
the Active Directory database. RODC was developed by Microsoft typically to be deployed in a branch office
environment.
RODC is a good option to enhance security by placing it in a location where physical security is poor. RODC can also
be placed at locations having relatively few users and a poor network bandwidth to the main site. As only the read-only
partition of the Active Directory database is hosted by RODC, a little local IT knowledge is required to maintain it.
Answer: A is incorrect. DNS dynamic update is used to enable DNS client computers for registering and dynamically
updating their resource records with a DNS server whenever any modification or change has been taken place. It is
used to
update the DNS client computers with the reflecting changes.
QUESTION 2
A digitally signed e-mail message:
A. Validates the recipient
B. Validates the sender
C. Is encrypted
D. Is virus-free
Correct Answer: B
By digitally signing a message, you apply your unique digital mark to the message. The digital signature includes your
certificate and public key. This information proves to the recipient that you signed the contents of the message and not
an imposter, and that the contents have not been altered in transit. Reference: http://office.microsoft.com/en-us/outlook-help/secure-messages-with-a-digital-signature-HP001230539.aspx
QUESTION 3
Which enables access to all of the logged-in user\\'s capabilities on a computer?
A. Java applets
B. ActiveX controls
C. Active Server Pages (ASP)
D. Microsoft Silverlight
Correct Answer: B
QUESTION 4
To keep third-party content providers from tracking your movements on the web, enable InPrivate Browsing.
Select the correct answer if the underlined text does not make the statement correct. Select "No change is needed\\'\\' if
the underlined text makes the statement correct.
A. InPrivate Filtering
B. SmartScreen Filter
C. Compatibility Mode
D. No change is needed
Correct Answer: A
QUESTION 5
You need to install a domain controller in a branch office. You also need to secure the information on the domain
controller. You will be unable to physically secure the server. Which should you implement?
A. Read-Only Domain Controller
B. Point-to-Point Tunneling Protocol (PPTP)
C. Layer 2 Tunneling Protocol (L2TP)
D. Server Core Domain Controller
Correct Answer: A
A read-only domain controller (RODC) is a new type of domain controller in the Windows Server?2008 operating
system. With an RODC, organizations can easily deploy a domain controller in locations where physical security cannot
be guaranteed. An RODC hosts read-only partitions of the Active Directory?Domain Services (AD DS) database.
References: http://technet.microsoft.com/en-us/library/cc732801(v=ws.10).aspx
QUESTION 6
For each of the following statements, select Yes if the statement is true. Otherwise, select No. Each correct selection is
worth one point.
Hot Area:
Correct Answer:

QUESTION 7
You want to make your computer resistant to online hackers and malicious software. What should you do?
A. Configure a forward proxy.
B. Install anti-virus software.
C. Enable spam filtering.
D. Turn on Windows Firewall.
Correct Answer: B
QUESTION 8
Which of the following helps prevent security failures?
A. Social engineering
B. Denial-of-Service attack
C. Attack surface reduction
D. Snooping
Correct Answer: C
The attack surface is a software environment where codes can be run by unauthenticated users. By improving
information security, the attack surface of a system or software can be reduced. Although attack surface reduction helps
prevent
security failures; it does not mitigate the amount of damage an attacker could inflict once a vulnerability is found.
Answer: B is incorrect. A Denial-of-Service (DoS) attack is mounted with the objective of causing a negative impact on
the performance of a computer or network. It is also known as network saturation attack or bandwidth consumption
attack.
Attackers make DoS attacks by sending a large number of protocol packets to a network. The problems caused by a
DoS attack are as follows: Saturate network resources.
Disrupt connections between two computers, thereby preventing communications between services.
Disrupt services to a specific computer.
Answer: D is incorrect. Snooping is an activity of observing the content that appears on a computer monitor or watching
what a user is typing. Snooping also occurs by using software programs to remotely monitor activity on a computer or
network device. Hackers or attackers use snooping techniques and equipment such as keyloggers to monitor
keystrokes, capture passwords and login information, and to intercept e-mail and other private communications.
Sometimes,
organizations also snoop their employees legitimately to monitor their use of organizations\\' computers and track
Internet usage.
Answer: A is incorrect. Social engineering is the art of convincing people and making them disclose useful information
such as account names and passwords. This information is further exploited by hackers to gain access to a user\\'s
computer or network. This method involves mental ability of people to trick someone rather than their technical skills. A
user should always distrust people who ask him for his account name, password, computer name, IP address,
employee
ID, or other information that can be misused.
QUESTION 9
Which password attack uses all possible alpha numeric combinations?
A. Social engineering
B. Brute force attack
C. Dictionary attack
D. Rainbow table attack
Correct Answer: C
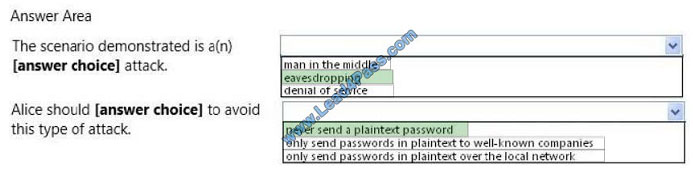
QUESTION 10
Alice sends her password to the game server in plaintext. Chuck is able to observe her password as shown in the
following image: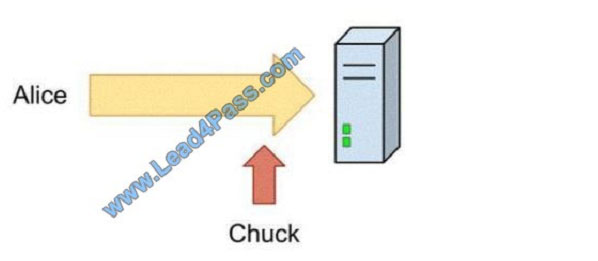
Use the drop-down menus to select the answer choice that completes each statement. Each correct selection is worth
one point.
Hot Area:

Correct Answer:
QUESTION 11
Mark works as the Network Administrator of a Windows 2000 based network. In order to reduce the administrative
burden and to optimize the network performance, he implements the DHCP and the DNS servers on the network. What
will he do integrate the working between the DHCP and the DNS servers? Each correct answer represents a part of the
solution. Choose two.
A. Configure the clients to use the DHCP server.
B. Enable DNS updates on the DHCP server.
C. Enable dynamic update on the DNS server.
D. Use the TCP/IP protocol on the network.
Correct Answer: BC
Answer: B and C To ensure proper DHCP-DNS integration, Mark must enable dynamic DNS support on the DNS server
as well as on the DHCP server. In the Windows 2000 Server, the DHCP service provides support to register and update
information for legacy DHCP clients in DNS zones. Legacy clients typically include other Microsoft TCP/IP client
computers that were released prior to Windows 2000 like Windows 9x, Windows NT. The DNS-DHCP integration,
provided in the Windows 2000 Server, enables a DHCP client that is unable to dynamically update DNS resource
records directly to have this information updated in the DNS forward, and reverse lookup zones by the DHCP server.
Note: Dynamic integration with the DHCP service is available only with Windows 2000 Server. DNS-DHCP integration is
not supported by DHCP servers running under Windows NT Server 4.0 and earlier versions.
QUESTION 12
The client computers on your network are stable and do not need any new features. Which is a benefit of applying
operating system updates to these clients?
A. Keep the software licensed
B. Keep the server ports available
C. Update the hardware firewall
D. Close existing vulnerabilities
Correct Answer: D
QUESTION 13
Ron owns the domain TechPerfect.net. He often receives bounces about messages he didn\\'t send. After looking at all
such mails, he is sure that someone is spamming e- mails and using his domain name. What will Ron do to ensure that
his domain name is not exploited?
A. Publish the MX record for the domain.
B. Publish the SPF record for the domain.
C. Publish the AAAA record for the domain.
D. Publish the A record for the domain.
Correct Answer: B
Sender Policy Framework (SPF) is an e-mail validation system designed to prevent e- mail spam by tackling source
address spoofing. SPF allows administrators to specify which hosts are allowed to send e-mail from a given domain by
creating a specific SPF record (or TXT record) in the public Domain Name System (DNS). Mail exchangers then use the
DNS to check whether that mail from the given domain is being sent by a host sanctioned by that domain\\'s
administrators. Answer: A, D, and C are incorrect. These records do not help prevent domain names from being
exploited by hackers.
Related 98-367 Popular Exam resources
| title | youtube | Microsoft | leads4pass | leads4pass Total Questions | |
|---|---|---|---|---|---|
| Microsoft IT Infrastructure | leads4pass 98-367 dumps pdf | leads4pass 98-367youtube | Exam 98-367: Security fundamentals - Microsoft | https://www.leads4pass.com/98-367.html | 277 Q&A |
| leads4pass 98-365 dumps pdf | leads4pass 98-365 youtube | Exam 98-365: Windows Server Administration Fundamentals | https://www.leads4pass.com/98-365.html | 400 Q&A |
leads4pass Year-round Discount Code
What are the advantages of leads4pass?
leads4pass employs the most authoritative exam specialists from Microsoft, Cisco, CompTIA, IBM, EMC, etc. We update exam data throughout the year. Highest pass rate! We have a large user base. We are an industry leader! Choose leads4pass to pass the exam with ease!
Summarize:
It's not easy to pass the Microsoft 98-367 exam, but with accurate learning materials and proper practice, you can crack the exam with excellent results. leads4pass.com provides you with the most relevant learning materials that you can use to help you prepare.